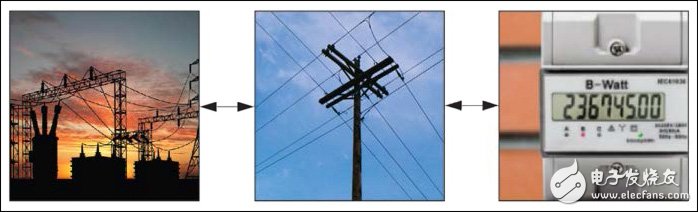
Meters and sensors are often scattered away from the power company's line of sight, and this article discusses various techniques to improve the safety of these smart grid endpoints. Both traditional physical and logical attacks are considered, as well as joint attacks that may penetrate the supply chain, which pose a serious threat to the power company's meter deployment. Security technologies to protect against these attacks have been successfully applied in the financial payment industry and can be reliably used for smart grid protection. As countries around the world compete to deploy intelligent transmission systems, how to ensure the safety of these systems has become an important issue. Although there are few standards specifically for smart grid security protection, power companies have begun to make a big fuss in the early stages of system deployment—equipped with IT systems for data collection and analysis, advanced communication technologies to transmit data, and endpoints (such as smart meters). Raw data is generated with the grid health monitoring system. Although security issues have become a widespread concern in recent years, there is still much work to be done, especially “endpoint†protection, such as the safety of electricity meters and grid sensors. This article provides an overview of the threats these endpoints face and the security technologies that address these threats. Figure 1. Smart Grid Model - Power companies collect data from endpoints over a communications network Security threat There is no doubt that the security grid faces many security risks, but it can be roughly divided into two categories. The first category is individual attack, which means that the attacker's goal is to use smart grid data to gain self-interest—for example, stealing electricity bills or concealing the production of illegal drugs. The purpose of individual attacks is not to disrupt grid management, but to gain the benefit of an individual or group. The second type of attack refers to activities that pose a threat to society, including activities that attempt to disrupt the operation of the grid. This may be an attack on the power grid itself (large area misreporting energy consumption, causing tension in the capital chain of the entire power grid); it may also be an attack on society (for example: terrorist attacks), causing power grids and power outages. In the event of a power outage, production and financial losses will be invaluable, especially in extremely hot, extremely cold climates, and pose a threat to human life. weakness Attackers often look at the entire grid and try to determine the best place to implement an attack in order to achieve the desired results with minimal investment and minimum risk. We can simply look at a "power center - endpoint" model and consider how the attacker can achieve the goal in both cases. Individual threat: For example, a hacker who wants to reduce the electricity bill, the attacker may mix into the power company control room and change his meter record to achieve the purpose; he may also intercept the data, intercept the energy consumption information sent to the power company; or directly tamper with The meter firmware makes it a record of reduced power consumption. Social threats: For example, terrorists who want to destroy the vast majority of users' power supply chains may attack an electric control room, remotely disconnect a large number of meters, or shut down a substation. The attacker may also inject instructions into the communication bus to perform similar actions; or control the meter to disconnect the relay directly from the remote end; it may also control the sensor to feed back error data to the power company, causing misjudgment and erroneous operation of the power control center. From the simple model, it can be seen that the attack path exists, and most of the entire power grid (power company control room, communication network, and endpoint) can implement the above attack behavior. Improving the overall security of the system provides security for the three links, but in practice it requires us to identify and locate the weakest link. This is exactly what the attacker is doing – finding the easiest point of intrusion (the weak link in the smart grid) to carry out the attack. Imagine how an attacker might look at the three main links. Successfully invading the power company's control room maximizes control of the grid, but it also carries the highest risks. The control room must be tightly guarded, have good access control, and have a secure certification process. In addition, intruders are difficult to hide in the control room - even if the security guards do not catch the intruder, the surveillance camera will record. Of course, insiders can most effectively attack the entire grid from the power control center, but because the power sector regulations strictly limit individual permissions, it is impossible for any individual to run operations that threaten the operation of the grid. Such operations usually require multiple people to be present at the same time. This simplifies the risk of internal staff committing crimes. In this way, the attacker's second choice must be the communication link. So far, most topics about smart grid security have focused on communication links, and most system deployments have adopted strict encryption technology to protect the smart grid. Data and command transmission between the endpoint and the power center. In order to successfully attack the communication channel, a security key or an authentication key must be obtained. A reliable communication protocol does not share a key, meaning that an attacker can only (1) obtain a key from a power company or endpoint; or (2) brute force on the channel's encryption/authentication mechanism. Note that option 1 is not actually attacking the channel itself, but attacking other parts of the grid. Violent attacks (option 2) are also unlikely to get results. Common encryption algorithms, such as AES-128, are violently attacked, and computational aspects are not feasible. This means that ultra-high-speed computers need to run for several years, even decades, to obtain keys, much longer than the data itself. the term. The attacker will then turn to the smart grid endpoint itself: devices such as smart meters or grid health monitoring sensors. Such devices are more attractive because the endpoint protection measures are relatively weak, widely dispersed outdoors, or mounted on long-distance transmission lines. We can take into account devices such as data concentrators, as such devices often have no protection. These weak points provide an opportunity for attackers to analyze and try different attack methods. Indeed, these terminals are electrically charged and difficult to reach (for example on towering transmission lines) and are potentially dangerous. But the attacker can take advantage of some protective measures to avoid personal injury. On the surface, endpoints like electricity meters are the easiest to attack. But how do opponents implement attacks? we are professional disposable vape manufacturer from shenzhen china and can offer one stop oem& odm vape service. Disposable vape pen,disposable electronic cigarette,vape pen,disposable ecigs,ecigs pen,e-cigs pen,vape pod,ELFBAR disposable vape pen is portable and fashion disposable electronic cigarette, disposable ecigs pen are trending featured vape pen for vapors as it's safety and easy to use. Disposable vape pod,disposable vape, wholesale vape,vape wholesale,vape pen manufacturer and supplier.disposable vape pen,disposable electronic cigarette,disposable ecigs pen,disposable ecigs stick,disposable e-cigs pen,disposable vape factory,disposable vape pod,disposable vape device,vape pen,vape stick, vape wholesale,wholesale vape,customized dispsoable vape pen,customized vape pen,OEM&ODM disposable ecigs pen,disposable electronic cigarette wholesale, wholesale disposable electronic cigarette,distribute vape pen,vape pen distribute,high quality vape pen,high quality vape pod. ELF BAR,Tpd Compliant Vapes,Original Onlyrelx Vape,Disposable E-Cigarette Onlyrelx,Vapeorizer Pen Shenzhen Onlyrelx Technology Co.,Ltd , https://www.onlyrelxtech.com